Where to focus your cyber security – episode 1
ICAS and Lugo have both conducted independent research projects in 2020 on the risks and opportunities presented by technology for the accountancy profession1.
This is one of a series of articles from our Commercial partners. The views expressed are those of the authors and not necessarily those of ICAS.
In this article, the first in a series of deeper dives into the key themes to come out of these studies, we look at cyber security and highlight five ‘top tips’ to make you more secure.
But first, let’s circle back on why this matters. In recent years, high profile examples of cyber security incidents have shown that the damage can be significant not only in terms of operational disruption and actual cost, but also reputational harm for the businesses involved.
The reality, and countless examples exist, is that those are the most susceptible to fall victim of cyber security breaches.
The ICAS research, unsurprisingly, found that cyber security, particularly in the context of increasing usage of cloud computing, was one of the top three concerns identified by respondents. The surprise came from Lugo’s research however2, where cyber security didn’t feature highly in terms of ‘wishes’ with only a few respondents’ wants being a ‘bulletproof security system’, ‘data security’ or ‘incident management’. Alarmingly also the majority of Lugo’s respondents rated themselves highly at 8 out of 10 for both their ‘awareness of cyber threats’ and ‘how secure they are’. This study highlighted as many as 70% of firms feeling secure enough, although 25% don’t have a communication plan in place if they do get breached.
Here’s a breakdown by size of firm based on the number of clients they have:
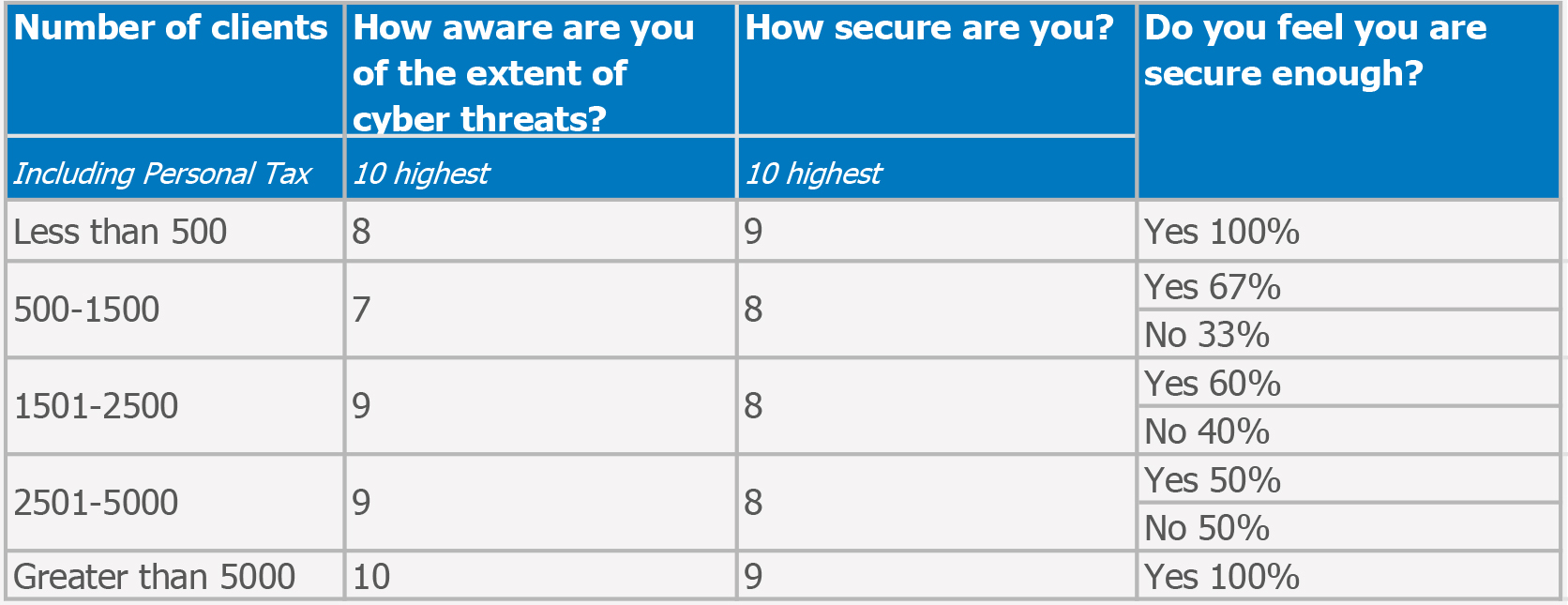
What both the ICAS and Lugo studies however highlight is the need to ensure everyone in the firm is educated on cyber security. Although smaller organisations are often more vulnerable and easier to hack, they also tend to underplay the risks by believing that bigger, higher profile organisations are the prime targets. So, what are our first 5 ‘top tips’ to increase cyber resilience?
Five key areas to boost your cyber resilience
Employee education
Employees are your greatest asset and your greatest liability, especially when it comes to keeping your systems secure. Staff pose the biggest risk as people make mistakes. Thankfully we haven’t been replaced with robots quite yet, so we need to ensure everyone in the firm remains vigilant at all times. Cyber training at all levels in your organisation should be an ongoing process including running simulated phishing attacks. We need to ‘Stay Alert’!
Education should be from the top down and you can show your commitment to securing and educating your firm by becoming Cyber Essentials certified
The National Cyber Security Centre (NCSC) offer free online training for staff, as they’ve found many SMEs don’t know the vital impact of cyber training, or where to start. Here’s the link to the interactive training which ends with an assessment consisting of 8 questions about the topics covered, to provide a knowledge check.
Education should be from the top down and you can show your commitment to securing and educating your firm by becoming Cyber Essentials certified. This government-backed scheme demonstrates to your staff and your clients that you are working to secure your IT against a cyber attack. The NCSC recommend five technical controls that you can put in place today, on their Cyber Essentials Advice page. As their trusted advisor, this is also an excellent scheme to recommend to your clients.
Cyber attacks can be difficult to spot and staff cannot be expected to identify them 100% of the time. The sooner an attack is reported, the quicker it can be resolved and the less damage it will cause. That’s why it’s so important to educate your team on how to report anything suspicious, with no negative consequences to them.
Phishing
If you’re caught off-guard you could easily be the victim of a phishing attack. Chances are you, or one of your colleagues, have seen one, if not been hit by one in the past. This is where scammers send fake emails asking for sensitive information (such as bank details) or containing links to bad websites.
A common one to watch out for is asking you to enter your Microsoft account credentials into a screen that looks very similar to the real thing. You should always check the email address of a message that asks you to click a link or download an attachment, as well as checking the full hyperlink to the link provided by hovering over it with your mouse. Various third party tools and packages also exist to help you with this.
For example, Lugo’s M365 Secure support package includes Microsoft 365 business premium which incorporates Microsoft Defender with the following features:
- Safe links: This helps protect your business against malicious sites when people click links in Office apps.
- Safe attachments: Provides an additional layer of protection for email attachments by checking attachments in email messages before they're delivered to recipients.
- Anti-phishing protection: Detects attempts to impersonate your users and internal or custom domains, and applying machine learning models and advanced impersonation-detection algorithms to avert phishing attacks.
Lots of guidance is available from the NCSC, the National Institute of Standards and Technology (NIST) and the Scottish Business Resilience Centre. You can also forward phishing attacks to report@phishing.gov.uk to report them to the NCSC.
Passwords
Gone are scheduled password changes, to be replaced with only changing passwords if there’s been a suspected compromise. Everyone should abide by your firm’s password policy which should now recommend a longer passphrase. Longer passphrases, even consisting of simpler words or constructs, are better than short passwords with special characters. Logins and passwords should never be shared. You could make use of a password manager tool to store complex passwords.
Multi-factor authentication (MFA)
Your passwords can nevertheless still be compromised. MFA immediately increases your account security by requiring multiple forms of verification to prove your identity when signing into an application. It’s free and easy and makes your account up to 99.9% less likely to be compromised. For your Microsoft account, MFA can be easily deployed across your firm enabling you to add a safe and secure two-step verification method for your online credentials from a range of authentication options (such as phone call, text message, or mobile app notification) to access your applications.
MFA is now widely available across many applications and should be switched on whenever you are given the option to do so. It is recommended to use an authenticator app over text message where possible, the latter becoming increasingly less secure.
Software
Firms should have an approved list of software that employees can install, with anything additional needing business case approval. This reduces the risk by only allowing supported software and making it easier to manage updates.
It is vital all operating systems are up to date, including servers, desktops, laptops, tablets and phones. All Windows 7 and Windows Server 2008/R2 customers received an update on 14th January 2020 as the operating systems were only in support until then and should no longer be in use. Once a Microsoft operating system reaches the end of support, customers will no longer receive security updates, leaving them exposed to hackers.
Don’t forget that cyber criminals are just that, criminals. Don’t punish yourself or a colleague for falling victim.
Web browsers, Office software, desktop software and anti-virus should all be set to automatically update. Users may have disabled, defer or decline updates, so it’s important to regularly check all devices that access corporate information are up to date. Updates should be installed promptly but, be aware, if the device is low on storage, the update may not complete.
We think that considering and starting to implement some of the tools we have just covered may be a good start for now. However, no matter how many different layers of security you utilise, you can still be the victim of cyber crime. Don’t forget that cyber criminals are just that, criminals. Don’t punish yourself or a colleague for falling victim.
Lugo partner with the Scottish Business Resilience Centre who, in partnership with the Scottish Government and Police Scotland, have launched the UK’s first Cyber Incident Response Helpline for the SME community and the third sector to help victims of cyber crime understand what support is immediately available to them and help them recover. They can help organisations confirm if they have been the victim of an attack and, if so, provide expert guidance to get them back to secure operations. Businesses can reach the Cyber Incident Helpline by calling 01786 437 472 weekdays 9am-5pm.
Look out for our next article on 16 February for 5 more ‘top tips’ on cyber security. In the meantime, if you’d like to discuss any element of this article, please email Liz.Smith@LugoIT.co.uk
References
1 Overview of Lugo’s research conducted on IT in Accountancy published in the last ICAS Technical Bulletin in November 2020 (you can access the article here)
2 The difference in research finding is attributable to the different target population interviewed in the ICAS and Lugo projects.
ICAS Insights: Top tips to strengthen your cyber security
Join us on Tuesday 23 February at 11am GMT when business IT specialists Lugo and a range of experts will share their cyber-resilience insights and top tips for improving your firm’s cyber security.
